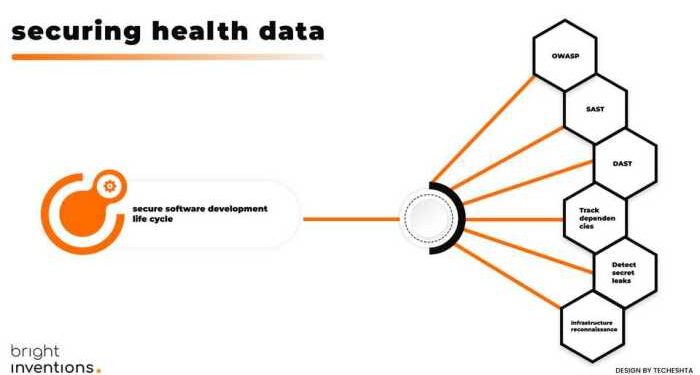
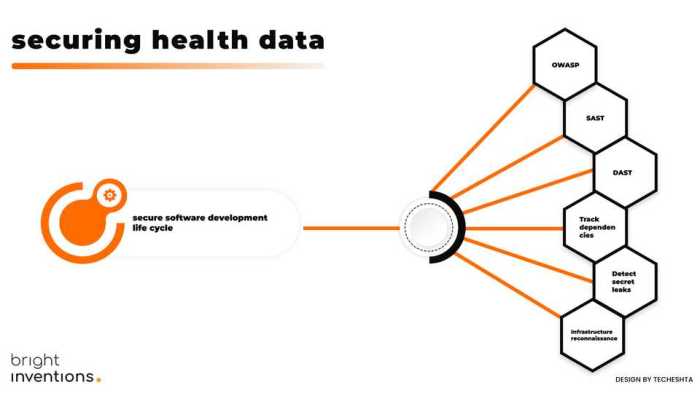
Embark on the journey of safeguarding health data with cloud technology in this informative piece that delves into the crucial aspects of data security and protection.
Explore the measures and strategies that ensure the confidentiality and integrity of sensitive health information in the digital realm.
Importance of Securing Health Data
In today's digital age, securing health data is of utmost importance to protect the privacy and confidentiality of patients' sensitive information. Any breach of this data can have severe consequences and jeopardize the well-being of individuals.
Potential Risks of Unauthorized Access
Unauthorized access to health data can lead to identity theft, fraud, and even medical errors. Cybercriminals can exploit this information for financial gain or to manipulate medical records, putting patients at risk of receiving incorrect treatment.
Legal Implications of Data Breaches
Healthcare organizations are legally obligated to safeguard patient data under laws like HIPAA (Health Insurance Portability and Accountability Act). Failure to comply with these regulations can result in hefty fines, lawsuits, and damage to the reputation of the institution.
Compliance and Regulations
When it comes to securing health data in the cloud, compliance with regulations is of utmost importance to protect sensitive information. Failure to adhere to these regulations can result in severe penalties and legal consequences for healthcare organizations.
Key Regulations Governing Health Data Security
- HIPAA (Health Insurance Portability and Accountability Act): HIPAA sets the standard for protecting sensitive patient data. It requires healthcare providers to implement safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information (ePHI).
- HITECH (Health Information Technology for Economic and Clinical Health Act): HITECH expanded on HIPAA's privacy and security requirements, emphasizing the importance of breach notifications and enforcing stricter penalties for non-compliance.
- GDPR (General Data Protection Regulation): Although originating in the EU, GDPR also impacts healthcare organizations worldwide that handle data of EU citizens. It focuses on data protection and privacy rights of individuals.
Requirements for Compliance with Regulations in Cloud Storage
- Implementing encryption mechanisms to protect data both in transit and at rest.
- Ensuring that cloud service providers have appropriate security measures in place and signing Business Associate Agreements (BAAs) to guarantee compliance with HIPAA.
- Conducting regular risk assessments and audits to identify vulnerabilities and address them promptly.
Consequences of Non-Compliance
- Financial penalties: Violating regulations such as HIPAA can result in hefty fines, ranging from thousands to millions of dollars, depending on the severity of the breach.
- Reputational damage: Healthcare organizations that fail to protect patient data risk losing the trust of their patients and stakeholders, leading to a tarnished reputation.
- Lawsuits and legal actions: Non-compliance can also expose organizations to lawsuits from affected individuals or regulatory bodies, resulting in costly legal battles and settlements.
Encryption and Data Protection
Encryption plays a crucial role in safeguarding health data stored on the cloud by converting sensitive information into a secure code that can only be accessed by authorized parties. This helps prevent unauthorized access and protects the confidentiality and integrity of the data.
Role of Encryption in Data Protection
- One common encryption method used in securing health data is AES (Advanced Encryption Standard), which is a symmetric encryption algorithm known for its robust security features.
- Another encryption technique is RSA (Rivest-Shamir-Adleman), which involves public and private keys to encrypt and decrypt data, providing a secure communication channel.
- End-to-end encryption is also widely used to ensure that data is encrypted from the point of origin to its destination, reducing the risk of interception or tampering.
Importance of Data Backup and Disaster Recovery
Data backup and disaster recovery strategies are essential components of securing health data on the cloud. By regularly backing up data to secure locations and implementing disaster recovery plans, healthcare organizations can ensure that critical information is protected in the event of data loss or system failures.
Data backup and disaster recovery strategies are like insurance policies for health data, providing a safety net in case of emergencies.
Access Control and Authentication
When it comes to securing health data in the cloud, access control and authentication play a crucial role in ensuring that only authorized individuals can view or manipulate sensitive information.
Importance of Multi-Factor Authentication
Multi-factor authentication adds an extra layer of security by requiring users to provide more than one form of verification before accessing health data. This significantly reduces the risk of unauthorized access, even if login credentials are compromised.
- Users may be required to enter a password, followed by a unique code sent to their mobile device.
- Biometric data, such as fingerprint or facial recognition, can also be used as an additional authentication factor.
- By implementing multi-factor authentication, healthcare organizations can better protect sensitive patient information from cyber threats.
Role-Based Access Control for Enhanced Security
Role-based access control (RBAC) is another best practice for managing access to health data in the cloud. This approach assigns specific roles to users and grants permissions based on their job functions and responsibilities.
RBAC ensures that individuals only have access to the data and resources necessary to perform their duties, reducing the risk of unauthorized access to sensitive information.
- Administrators have full access to health data and system settings, while clinicians may have restricted access to patient records for treatment purposes.
- RBAC helps enforce the principle of least privilege, limiting user access rights to the minimum level required to perform their tasks.
- Regularly reviewing and updating role assignments is essential to maintaining data security and preventing unauthorized access.
Security Monitoring and Incident Response
Continuous monitoring is crucial for detecting potential security threats in the healthcare sector. With the sensitive nature of health data, any breach or unauthorized access can have severe consequences. By actively monitoring systems and networks, healthcare organizations can identify any anomalies or suspicious activities in real-time, allowing them to respond promptly and mitigate risks.
Incident Response Planning
- Establish a dedicated incident response team: Designate specific individuals responsible for managing and responding to security incidents.
- Develop an incident response plan: Create a detailed plan outlining the steps to be taken in case of a data breach, including containment, eradication, and recovery procedures.
- Conduct regular training and drills: Ensure that all team members are well-prepared to execute the incident response plan effectively through training sessions and simulated exercises.
- Coordinate with external stakeholders: Collaborate with law enforcement, regulatory authorities, and other relevant parties to address the breach and comply with reporting requirements.
Role of Security Audits and Assessments
Security audits and assessments play a vital role in maintaining the integrity of health data. These processes involve evaluating the effectiveness of security controls, identifying vulnerabilities, and implementing necessary measures to enhance data protection. By regularly conducting audits and assessments, healthcare organizations can proactively identify weaknesses in their security posture and address them before they are exploited by threat actors.
Wrap-Up
In conclusion, adopting the best practices Artikeld here is paramount in maintaining the trust and security of health data in the ever-evolving landscape of cloud technology.
FAQ Guide
What are the risks of unauthorized access to health data?
Unauthorized access can lead to breaches of confidentiality and privacy, compromising the integrity of sensitive information.
How does encryption protect health data on the cloud?
Encryption scrambles data into a coded format that can only be decrypted with the proper key, ensuring that even if data is intercepted, it remains unreadable.
Why is multi-factor authentication important for preventing unauthorized access?
Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of verification before accessing sensitive health data.
What is the significance of security audits in maintaining data integrity?
Security audits help identify vulnerabilities and gaps in data security measures, allowing organizations to address them proactively and maintain the integrity of health data.